Cybersecurity in 2025: 16 Billion Records Leaked — What You MUST Do Now
Overview
📢 Introduction: The Biggest Data Breach in History
In June 2025, the world witnessed something never seen before — a massive data leak that exposed over 16 billion personal records. This breach is now being called the largest in internet history. It didn’t just affect big companies — it put millions of people like you at risk. If you've ever used your email, social media, or online shopping, your private information may now be in the hands of hackers.
This is not just a tech story. It’s a global crisis. It affects your safety, your money, and even your identity. In this article, we’ll break down what happened, why it’s serious, and what you must do right now to stay safe.
Cybersecurity experts discovered that many companies had stored their customer data on cloud platforms — but without proper security. This means the databases were left open to the public, and anyone could access or download the data.
The leaked information wasn’t just from one source. It came from thousands of databases across industries like banking, healthcare, education, online shopping, government, and social media. Some databases were old, but many were active, meaning users were still using the same accounts and passwords today.
Here’s what the leaked data included:
- Full names
- Email addresses
- Mobile numbers
- Passwords (many in plain text)
- Home addresses
- Government IDs
- Biometric data like fingerprints and facial scans
Once exposed, this data was uploaded and sold on dark web forums, where criminals from around the world buy and trade stolen information.
👥 Who will affected ?
The simple answer is: everyone. The damage from this breach goes beyond companies — it reaches regular people and even national governments.
🏢 1. Businesses
Companies lost sensitive customer data, trade secrets, and in many cases, trust. They now face legal issues, fines, and reputation damage. Many small businesses may not even survive the fallout. Data leaks can destroy customer loyalty and business operations overnight.
👤 2. Individuals
This is where it gets personal. If your data was leaked:
- Hackers can access your social media or email
- Scammers can take loans or create fake accounts in your name
- You can lose money through fraud or phishing
- Even your fingerprint or face scan, once leaked,
cannot be changed— unlike a password.
🏛️ 3. Governments
Some of the leaked data came from public and government systems. This can be used for cyber espionage, attacks on critical infrastructure, or political manipulation.
⚠️ Why Should Non-Tech Users Worry?
Even if you don’t work in tech or understand cybersecurity, this still affects you. If you use WhatsApp, Instagram, Gmail, online shopping, or bank apps — you have data that can be stolen or misused. And you may not even know it's already leaked.
💣 Real-World Dangers of This Leak
This breach can lead to serious, real-world consequences. Here are just a few:
1. Identity Theft
Someone can use your personal information to pretenting like you. They might apply for a SIM card, open a bank account, or even get a loan in your name.
2. Financial Fraud
If your banking info or OTP methods are compromised, your money can be stolen through fake transactions.
3. Scams & Phishing
Leaked emails and phone numbers are used to send fake messages. These messages might look real and ask for OTPs, passwords, or payments. If you click these phishing links, your device could be infected or your account hijacked.
4. Social Engineering
Hackers now know your name, number, family details, and more. They can call you pretending to be a bank or government officer. Many people fall for these traps because the information sounds too accurate to question.
🛡️ What You MUST Do Now to Stay Safe
This situation is serious, but you’re not helpless. Here’s what you can do right now:
✅ 1. Check if You’re Affected Visit Cyber Security Tools like:
Just enter your email. If it shows you’ve been exposed in a breach, act fast.
✅ 2. Change All Your Passwords
Use unique, strong passwords for every account. Avoid using the same password on multiple sites.
Tips for strong passwords:
- At least 12 characters
- Mix of letters, numbers, and symbols
- Avoid using your name, birthdate, or mobile number
✅ 3. Turn On 2FA (Two-Factor Authentication)
2FA adds an extra step when logging in — usually a code sent to your phone or email. Even if someone steals your password, they can’t log in without verification code.
Turn on 2FA for:
- Gmail and email apps
- Instagram, Facebook, WhatsApp
- Bank and payment apps
✅ 4. Avoid Public Wi-Fi Without VPN
Free Wi-Fi in cafés, malls, or stations is often unsecured. Hackers can easily steal your data while using these networks. Use a VPN app to stay protected if you have to use public internet.
✅ 5. Stay Alert for Phishing and Scam Calls
Don’t click on unknown links in messages or emails. Never share OTPs or passwords on calls — even if they say they're from your bank or a government office. s
🧠 Why Did This Happen?
This disaster didn’t need high-level hacking. It happened because of:
- Unprotected cloud storage
- No encryption on sensitive data
- No password protection on some databases
- Outdated software with known bugs
- Companies who failed basic security checks
In simple words, some companies made careless mistakes, and billions of users are paying the price.
🚨 What’s Next? Cybersecurity in 2025 and Beyond
The cyber world is changing fast. Even as you read this, hackers are developing new methods — and they’re using AI to attack faster and smarter.
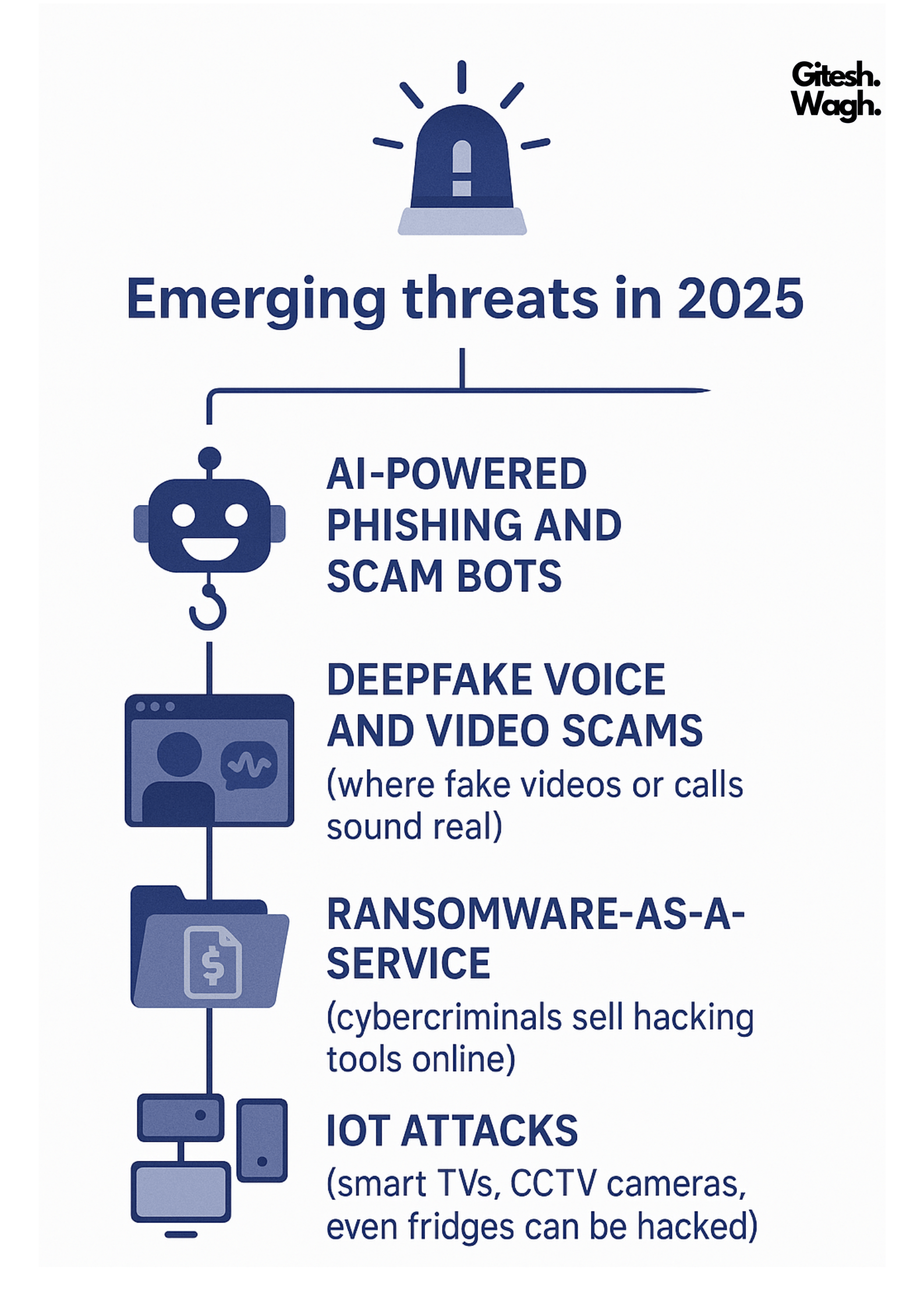
Emerging threats in 2025:
AI-powered phishing and scam botsDeepfake voice and video scams(where fake videos or calls sound real)Ransomware-as-a-Service(cybercriminals sell hacking tools online)IoT attacks(smart TVs, CCTV cameras, even fridges can be hacked)
We are entering a world where cybersecurity is just as important as physical security. Everyone, not just tech experts, needs to stay aware and take action.
📊 Shocking Stats You Should Know
| 📌 Stat | 💬 Explanation & Source |
|---|---|
| 16.2 billion records leaked | Based on breach reports from June 2025, especially a global 16B+ record leak. Reported by cybersecurity media like Cybernews, Hackread, and BleepingComputer. |
| 88% of people reused passwords | From Google Online Security Survey and NordPass Password Habits Report (2022–2023), showing that over 80% of users reuse passwords. |
| 73% didn’t enable 2FA | As per Duo Security's Trusted Access Report and studies by Authy/LastPass, only ~20–30% of users globally use two-factor authentication. |
| ₹1.4 lakh (~$1,700) avg. loss | Based on IBM’s Cost of a Data Breach Report 2023 and Norton Cyber Safety Insights Report, which estimate the average financial loss per identity theft victim. |